The U.S. Department of Justice (DoJ) on Wednesday claimed it demolished what it termed as "likely the world's largest botnet ever," which comprised of an army of 19 million infected devices that was leased to other threat actors to execute a broad variety of crimes.
The botnet, which has a worldwide presence covering more than 190 nations, functioned as a residential proxy service known as 911 S5. A 35-year-old Chinese citizen, YunHe Wang, was detained in Singapore on May 24, 2024, for developing and operating as the chief administrator of the illicit website from 2014 until July 2022.
Wang has been charged with conspiracy to conduct computer fraud, substantial computer fraud, conspiracy to commit wire fraud, and conspiracy to commit money laundering. If convicted on all charges, Wang faces a maximum punishment of 65 years in jail.
The Justice Department claimed the botnet was used to carry out cyber attacks, financial fraud, identity theft, child exploitation, harassment, bomb threats, and export violations.
It's worth mentioning that Wang was identified as the owner of 911 S5 by security writer Brian Krebs in July 2022, after which the business unexpectedly shut down on July 28, 2022, alleging a data breach of its essential components.
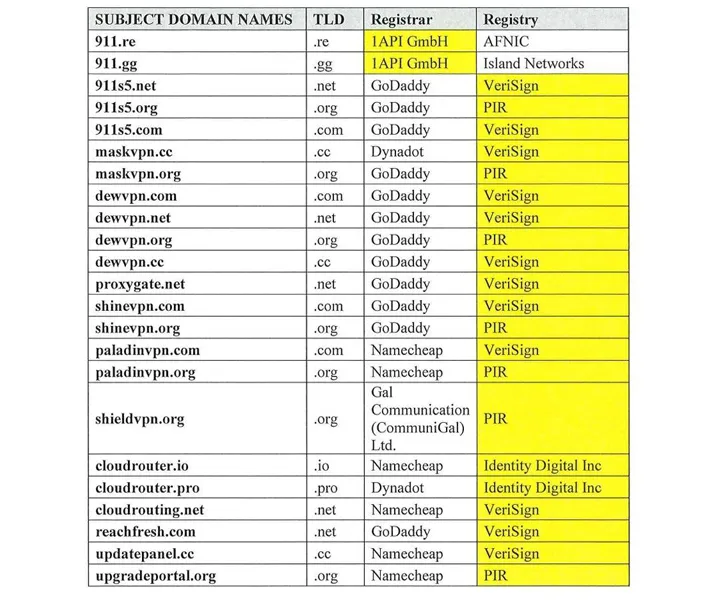
Although it was relaunched under a new brand name called CloudRouter a few months later, according to Spur, the service has now halted operations during this past weekend, the cybersecurity company's co-founder Riley Kilmer told Krebs.
"Wang and others are alleged to have created and disseminated malware to compromise and amass a network of millions of residential Windows computers worldwide," according to an unsealed indictment.
"These devices were connected with more than 19 million distinct IP addresses, including 613,841 IP addresses residing in the United States. Wang subsequently produced millions of dollars by selling thieves access to these corrupted IP addresses for a price."
Residential proxies (RESIPs) are networks of legal consumer devices that route traffic on behalf of paying users. It often includes the providers renting access to reroute network traffic via laptops, cellphones, or routers belonging to genuine people.
The major purpose of utilizing such proxyware is to divert traffic via the IP addresses of these devices so as to anonymize the source of the malicious requests.
Court records accuse Wang of allegedly spreading the virus using free Virtual Private Network (VPN) applications, such as MaskVPN and DewVPN, as well as other pay-per-install businesses that packaged it with unlicensed software.
The defendant is claimed to have overseen an infrastructure including 150 servers globally, 76 of which were seized from U.S. based internet service providers.
"Using the dedicated servers, Wang deployed and managed applications, commanded and controlled the infected devices, operated his 911 S5 service, and provided paying customers with access to proxied IP addresses associated with the infected devices," the DoJ stated.
It's also alleged that 911 S5 allowed criminal actors to bypass financial fraud detection systems and steal billions of dollars from financial institutions, credit card issuers, and federal lending programs, including pandemic relief and the Economic Injury Disaster Loan (EIDL) program, by submitting fraudulent claims that originated from compromised IP addresses.
Furthermore, the site made it feasible for attackers located outside the U.S. to buy items using stolen credit cards or criminally obtained money, and unlawfully export them outside of the nation in breach of U.S. export rules.
Wang, for his part, is estimated to have received approximately $99 million from selling access to the hijacked proxied IP addresses, using the ill-gotten money to purchase four luxury cars, several expensive wristwatches, and 21 residential or investment properties across the U.S., China, Singapore, Thailand, and the U.A.E.
Other digital assets possessed by Wang include over a dozen local and foreign bank accounts and more than 24 bitcoin wallets, which were utilized to carry out the plan. Blockchain analytics company Chainalysis found that the addresses connected with Wang have $136.4 million in cryptocurrencies.
The takedown, a consequence of a joint action by U.S., Singapore, Thailand, and Germany, has led in the interruption of 23 domains and over 70 servers that represent the core of 911 S5. The operation also witnessed the confiscation of assets worth at around $30 million.
Concurrent with Wang's indictment, the Department of the Treasury's Office of Foreign Assets Control (OFAC) levied sanctions against the defendant along with his co-conspirator Jingping Liu and power of attorney Yanni Zheng for their activities associated with the 911 S5 botnet and the residential proxy service.
The agency also sanctioned three Thailand-based entities, namely Spicy Code Company Limited, Tulip Biz Pattaya Group Company Limited, and Lily Suites Company Limited, that are said to be owned or controlled by Wang, noting that Spicy Code Company Limited was used to buy real estate properties in the country.
"The conduct alleged here reads like it's ripped from a screenplay: A scheme to sell access to millions of malware-infected computers worldwide, enabling criminals over the world to steal billions of dollars, transmit bomb threats, and exchange child exploitation materials," said Matthew S. Axelrod of the U.S. Department of Commerce's Bureau of Industry and Security (BIS).
"What they don't show in the movies though is the painstaking work it takes by domestic and international law enforcement, working closely with industry partners, to take down such a brazen scheme and make an arrest like this happen."