Europol on Thursday announced it took down the infrastructure related with multiple malware loader operations such as IcedID, SystemBC, PikaBot, SmokeLoader, Bumblebee, and TrickBot as part of a joint law enforcement action called Operation Endgame.
"The actions focused on disrupting criminal services through arresting High Value Targets, taking down the criminal infrastructures and freezing illegal proceeds," Europol said in a statement. "The malware [...] facilitated attacks with ransomware and other malicious software."
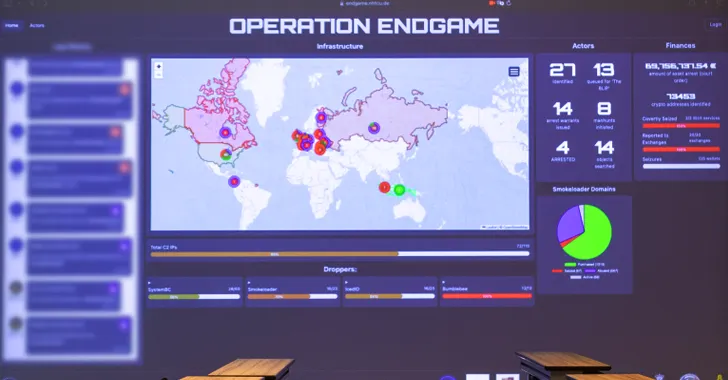
The activity, which took place between May 27 and May 29, has resulted in the disassembly of over 100 servers globally and the arrest of four persons, one in Armenia three in Ukraine, after searches across 16 sites in Armenia, the Netherlands, Portugal, and Ukraine.
The servers, according to Europol, were situated in Bulgaria, Canada, Germany, Lithuania, the Netherlands, Romania, Switzerland, Ukraine, the United Kingdom, and the United States. More than 2,000 domains have been taken by legal enforcement.
One of the key suspects is believed to have gained at least €69 million ($74.6 million) by renting out criminal infrastructure sites to install ransomware.
"Via so-called 'sinkholing' techniques or the use of tools to access the systems of operators behind the malware, investigators managed to block and take down the botnets," Eurojust claimed.
Separately, German officials are pursuing the arrest of seven persons linked with a criminal group whose objective was to distribute the TrickBot virus. An eighth individual is suspected of being one of the ringleaders of the organization behind SmokeLoader.
According to the U.S. Federal Bureau of Investigation (FBI), the malware organizations are suspected to have infected millions of computers throughout the globe. This constituted an undisclosed hospital network, which "not only cost millions of dollars but alarmingly put people’s lives at risk due to the compromised critical care online system."
Enterprise security Proofpoint informed The Hacker News that it supplied information with law enforcement on the botnet architecture as well as the inner workings of the malware artifacts, "identifying patterns in how the threat actors set up their servers."
Loaders, also known as droppers, are malicious software used to obtain initial access and transfer further payloads onto infected computers, including ransomware variations. They are often disseminated by phishing efforts, hijacked sites, or packaged with popular software.
"Droppers are designed to avoid detection by security software," Europol added. "They may use methods like obfuscating their code, running in memory without saving to disk, or impersonating legitimate software processes."
"After deploying the additional malware, the dropper may either remain inactive or remove itself to evade detection, leaving the payload to carry out the intended malicious activities."
The agency touted the takedowns as the largest-ever operation against botnets, including officials from Armenia, Bulgaria, Denmark, France, Germany, Lithuania, the Netherlands, Portugal, Romania, Switzerland, Ukraine, the United Kingdom, and the United States.
"Law enforcement continue their impressive run of takedown operations with an impressive operation against the loader ecosystem," Don Smith, vice president of Threat Intelligence, Secureworks Counter Threat Unit (CTU), stated in a statement posted with The Hacker News.
"Individually these operations have been significant, in concert they demonstrate that whilst the malicious actors may be out of reach of the courts, their botnets and infrastructure is not, it can be compromised and taken offline."
"We're never going to get to the kernel of some of these organized criminal gangs, but if we can minimize the impact they have by reducing their ability to scale, their ability to deploy, then that's a good thing."
(The report was modified after publication with new comments from Proofpoint and Secureworks.)